The Need for On-Premises & In-Cloud Collaboration
NETSCOUT Adaptive DDoS Protection Strategy leverages a robust, always-on, on-premises solution specifically designed to automatically identify and neutralize all types of DDoS attacks against enterprises and service providers. Adapting to the escalating intensity and complexity of cyber threats ensures unimpeded access to your business-critical services. This strategy incorporates intelligent systems that swiftly detect and counteract threats, preventing potential disruptions before they affect the availability and performance of your vital network infrastructure. This proactive approach provides a robust shield, ensuring your enterprise is always protected against evolving cyber threats.
Although traditional cloud-based DDoS protection solutions, including those provided by ISPs or CDNs, are designed to stop large volumetric DDoS attacks, they struggle to eliminate other types of DDoS attacks designed to evade their efforts. Cloud-based DDoS defense solutions augment on-premises protection. On-premises DDoS attack mitigation has capabilities intended to identify and protect against attacks designed to circumvent cloud-based solutions.
Furthermore, due to the dynamic, multi-vector nature of modern-day DDoS attacks, the best practice is to employ both an on-premises and a cloud solution with an intelligent and automated integration that offers dynamic, adaptable DDoS protection.

An On-Premises Adaptive DDoS Protection Solution Should be a Priority
Industry analysts are coming to grips with the fact that due to today’s growing frequency and dynamic nature of DDoS attacks, the need for a multilayer, adaptable DDoS protection strategy is now a requirement. Furthermore, due to the creation of new attack vectors like Dynamic DDoS Attacks, which change vectors based on the defense that is presented, the need for On-Premises DDoS attack mitigation real-time in-line attack analysis is a priority.
Excellent tool. Before installing NETSCOUT Arbor we were unaware of the amount of unwanted traffic hitting our network. Being able to block these has definitely given our firewall some breathing space.
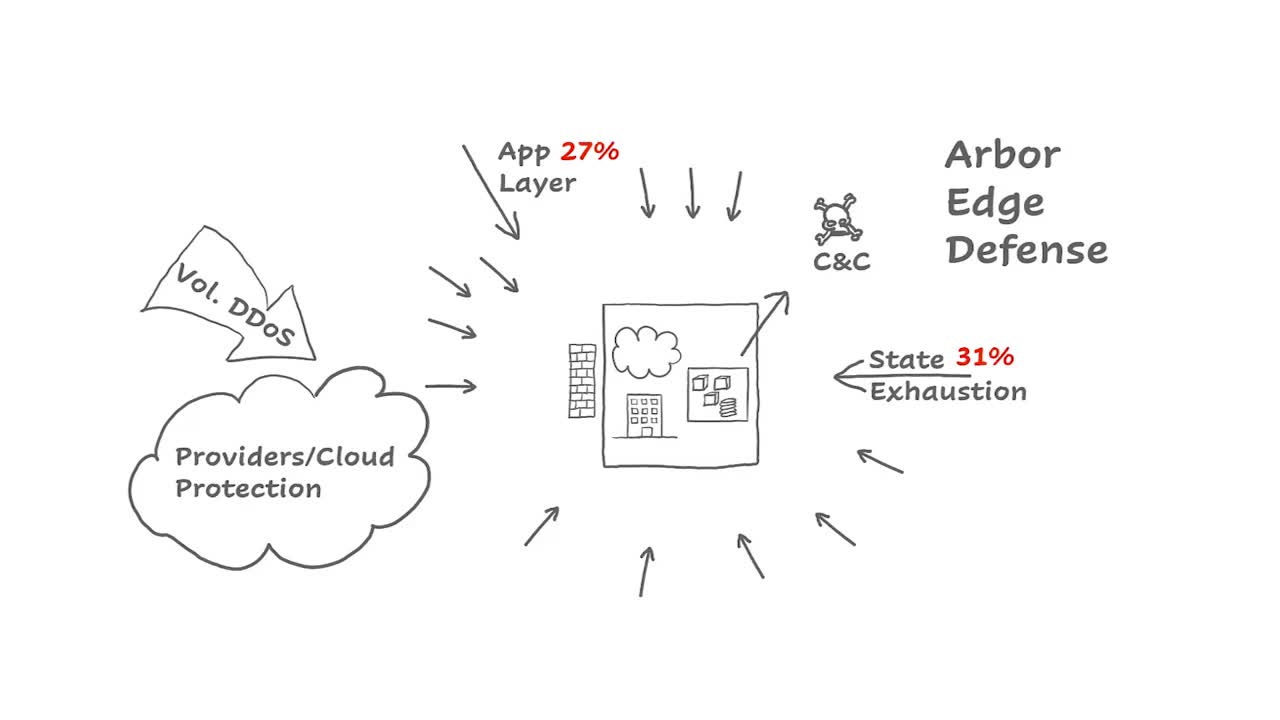
Why On-Premises Protection Should Be The Foundation of an Adaptive DDoS Mitigation Strategy
On-Premises DDoS Attack Protection
NETSCOUT Arbor DDoS Attack protection solution is an intelligently automated combination of in-cloud and on-premises DDoS attack protection that is continuously backed by global threat intelligence and expertise.
Stopping Application Layer Attacks
Because application layer attacks are typically made up of lower volume traffic, they do not automatically trigger volumetric monitors employed by cloud scrubbing solutions and require on-premise devices like Arbor Edge Defense (AED) to automatically detect and mitigate.
DDoS Protection for Stateful Devices
Stateful devices within your network like NGFWs, VPN Concentrators, and Load Balancers are common targets for state exhaustion attacks. Protecting them in an always-on manner can only be accomplished with an On-Premise stateless device like Arbor Edge Defense.
Blocking Internal & External C2 Communications
Once an attacker breaches your network, compromised internal devices will communicate with their command-and-control infrastructure for further instructions. Deployed outside your firewall, Arbor Edge Defense (AED) blocks Indicators of Compromise (IoC), acting as a last line of defense for your organization.
Stopping Attacks in Encrypted Traffic
When cybercriminals embed attacks within encrypted traffic, the only way to detect them is through decryption. Unlike decryption in the cloud, a safer method is to utilize the on-premises, embedded decryption capabilities in Arbor Edge Defense (AED).
DNS DDoS Protection
DNS water torture attacks rose from an average of 144 daily attacks at the start of 2023 to 611 at the end of June, marking a nearly 353 percent increase in only six months. AED detects DNS attacks based on an increase in NXDOMAIN or SERVFAIL entries in DNS query responses. During the attack, AED provides an effective and unique solution in multiple ways. First, it compares the hostname in every query against the list of auto-learned valid hostnames while also identifying which zones are under attack. Second, if there is a match, the validated traffic is passed. If there’s a miss or an alert, and if it’s in the zones that are under attack, AED blocks that traffic.
2022 CyberSecured Award Winner: Network Security
AED has definitely improved uptime for applications that are bringing business value to the company.
-Manager of Cyber Defense Center Engineering for a logistics firm



